Key Takeaways
- Endpoint security is crucial for protecting data from cyber threats.
- It involves various components such as antivirus software, firewalls, and encryption.
- Implementing endpoint security offers benefits like data protection, compliance, and reduced risk of cyber attacks.
- AI and machine learning are shaping the future of endpoint security.
Introduction
In the modern digital landscape, endpoint security has become a cornerstone of cybersecurity strategies for individuals and organizations. As cyber threats continue to evolve and grow in number, protecting data isn’t just an option—it’s a necessity. Endpoint security offers several layers of protection designed to safeguard your data from a wide array of threats, thereby ensuring the privacy and integrity of sensitive information. This article explores how endpoint security functions and why it’s essential in today’s interconnected world.
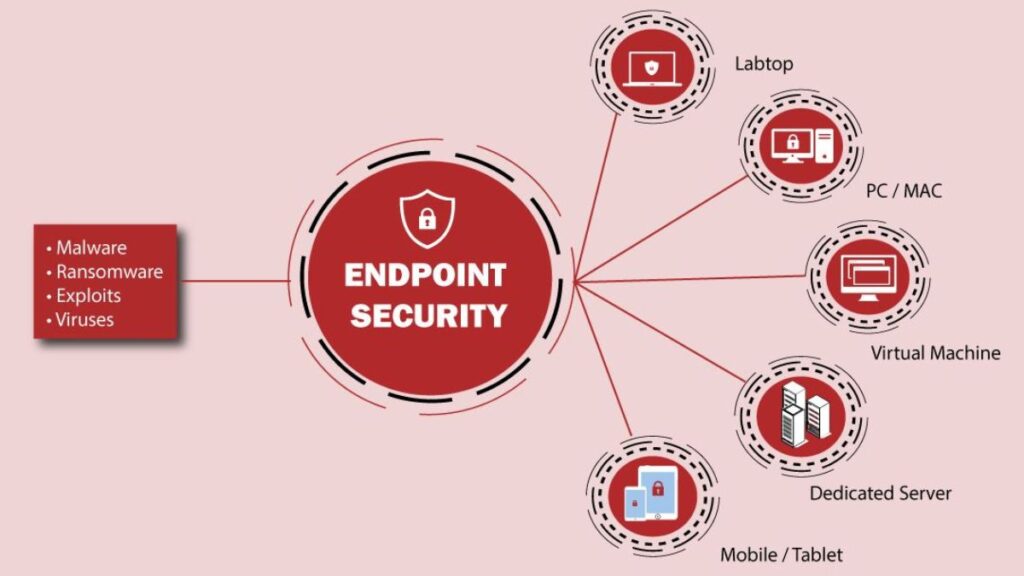
The Mechanism of Endpoint Security
The primary function of endpoint security is to secure end-user devices such as laptops, desktops, smartphones, and tablets from malicious activities. Endpoint security encompasses a mixture of software and hardware solutions that work together to safeguard these devices against cyber threats. Understanding its key components gives us insight into how endpoint security protects our data.
Antivirus Software
Antivirus software frequently serves as the first line of defense in endpoint security. Its purpose is to find, isolate, and get rid of malware. It scans incoming files and matches them against a database of known threats, ensuring that malicious software is intercepted before it can cause harm. Regular updates keep the antivirus software’s database current, enabling it to recognize and defend against new threats.
Firewalls
Firewalls act as barriers between trusted internal networks and untrusted external networks. They use preset security rules to monitor and manage all incoming and outgoing network traffic. By blocking unauthorized access while permitting legitimate communication, firewalls prevent attackers from exploiting vulnerabilities within the network.
Endpoint Detection and Response (EDR)
EDR solutions provide real-time monitoring and response capabilities, allowing for rapid identification and mitigation of cyber threats. These solutions can identify unusual patterns of behavior that may indicate a cyber attack and enable security teams to respond swiftly, reducing the potential impact of the threat.
Data Encryption
Data encryption ensures that even if cybercriminals access the data, they cannot read it without the decryption key. Data is encoded so only authorized parties can access it in a coded format. This provides extra security, especially for sensitive data like bank account information, unique personal identification numbers, and private correspondence.
Benefits of Endpoint Security
Implementing robust endpoint security measures offers many benefits, ensuring comprehensive protection of your digital environment. Here’s how:
Data Protection
One of the primary benefits of endpoint security is protecting sensitive data from breaches and leaks. Effective endpoint security solutions safeguard personal and organizational data against unauthorized access, preventing identity theft, financial loss, and data corruption.
Enhanced Compliance
Many industries are governed by strict regulations concerning data protection. Endpoint security guarantees that data is transferred and stored securely, which assists enterprises in adhering to these legal obligations. In addition to preventing legal issues, compliance improves the organization’s standing and credibility.
Reduced Risk of Cyber Attacks
Endpoint security reduces the risk of cyber attacks by incorporating multiple layers of defense mechanisms. Minimizing vulnerabilities and attack surfaces makes it harder for cybercriminals to infiltrate the system. Effective endpoint security measures act as a deterrent against potential attacks, thereby reducing the frequency and severity of security incidents.
Improved Device Management
Endpoint security streamlines the management of devices within a network. Centralized management tools allow security teams to monitor all endpoints from a single interface, simplifying updating software, enforcing security policies, and responding to threats. This centralized approach frees up resources for other crucial tasks by reducing the administrative load and ensuring consistency.
The Challenges of Endpoint Security
While endpoint security is essential for protecting data, implementing it is challenging. Understanding these difficulties is vital for creating effective security plans.
Diversity of Devices
Organizations often use various devices with different operating systems and security requirements. Managing the security of this diverse array of devices can be complex. Endpoint security must be versatile and adaptive to accommodate various configurations and ensure consistent device protection.
Real-Time Protection
Another significant challenge is achieving continuous monitoring and real-time protection without impacting device performance. Security solutions must be designed to operate efficiently, balancing robust protection with minimal resource consumption to avoid hampering user productivity.
Sophisticated Threats
Cyber threats are becoming increasingly sophisticated, requiring constant evolution of security measures. Threat actors continuously develop new techniques to bypass security measures, and staying ahead of these evolving threats requires advanced threat detection and proactive defense mechanisms. Endpoint security solutions must be continually updated to address new vulnerabilities and counter emerging threats.
Tips for Enhancing Endpoint Security
To bolster your endpoint security, consider implementing the following tips:
- Regular Software Updates: Ensure that all software and operating systems are regularly updated to protect against known vulnerabilities. Automatic updates can simplify this process by ensuring that updates are applied as soon as they are available.
- Strong Password Policies: Implement complex password requirements and enforce regular password changes. Promote the use of password managers to create and maintain solid, unique passwords for every account.
- User Education: Train employees to recognize phishing scams and other social engineering attacks. Regular training sessions allow everyone to stay updated on the newest threats and the best ways to avoid them.
- Multi-Factor Authentication (MFA): Demanding multiple forms of authentication can add extra protection. Even if an attacker manages to get a user’s password, MFA makes it much more difficult for them to gain access.
- Backup Data Regularly: Maintaining regular data backups guarantees you can recover your data during a ransomware attack or other data loss catastrophe. Ensure backups are kept in a safe location and routinely verified for accuracy.
The Future of Endpoint Security
Emerging technologies like artificial intelligence (AI) and machine learning (ML) will impact endpoint security in the future. These technological developments depend on better threat identification and mitigation. AI and ML can examine large data sets to spot unusual patterns and potential threats before they have a chance to cause harm.
Security systems are better equipped to recognize and react to sophisticated attacks thanks to AI and ML, which allow them to learn from previous mistakes and adjust to new threats. Integrating these technologies into endpoint security frameworks can significantly improve threat detection capabilities and reduce response times. The continual advancement of AI and ML technologies will further enhance the effectiveness of endpoint security solutions.
Conclusion
Endpoint security is a vital component of a comprehensive cybersecurity strategy. By implementing best practices and comprehending their workings, people and companies can safeguard their data from various threats. Proactive and adaptable security measures are essential for preserving the integrity and privacy of digital data because cyber threats are constantly changing.
Investing in endpoint security strengthens an organization’s overall cybersecurity posture and protects against possible breaches. Sturdy endpoint security is crucial for guaranteeing the confidentiality and integrity of sensitive data in a world where cyber threats are growing more complex and common. Organizations can successfully protect their digital assets and drastically lower their risk exposure by implementing a multi-layered approach to endpoint security.